DNS publishing over COSMOTE, is not any more supported?
February 17, 2017
Creative People Receives Two Separate Five-Star Reviews
July 18, 2019The cause of this seems to be that when a user logs out from Windows 10 sets some essential registry keys to read only. When they logon again these keys are in the wrong state and packaged applications including Edge fail to load. But this seems to be on of the causes, while MS has no fix released since version 1511.
The below is a walkthrough for working this out.
Step1
Make sure your WKS has all latest updates.
Connect to your DC and open the group policy editor
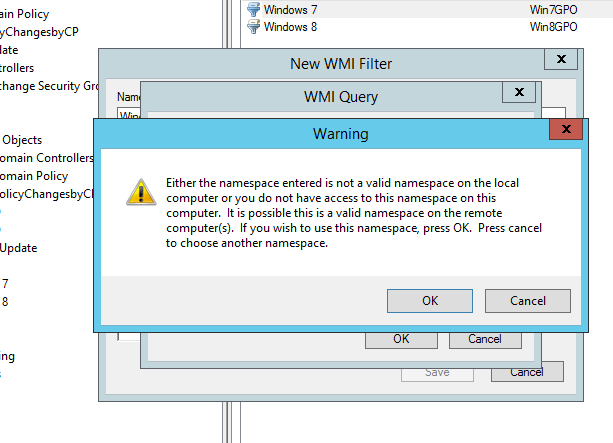
Create a WMI filter for Windows 10 and put the following
Namespace (should be already there): root\CIMv2
Query: select * from WIN32_OperatingSystem WHERE Version LIKE ‘10.0.%’
You may get the following message, ignore it.
Step2
CREATE A GROUP POLICY TO APPLY THIS AS A LOGON SCRIPT
Create a group policy for your domain users called “User-Windows10RoamingProfileFix”. This will be targeted to Windows 10 computers using the WMI filter we created in the previous step.
On the new policy Right Click> Enforced
Right Click > Edit > User Configuration > Policies > Windows Settings > Scripts (Logon/Logoff) > Double Click on Logon > PowerShell Scripts > Add
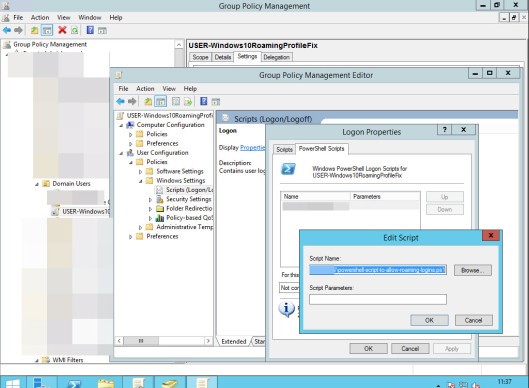
Click on Browse
Inside the browse popup menu create a new txt file and rename it to
POWERSHELL-SCRIPT-TO-ALLOW-ROAMING-LOGINS.PS1
Make sure you have file extensions on and the file is a ps1 extension (powershell) and not a txt!
Copy paste the following inside the file:
#!PowerShell. De pilo pendet.
#(c) Christian Ullrich
# copied by James Bayley 2016/01/25
function MakeACE() {
# S-1-15-2-1 is WELL_KNOWN_SID_TYPE::WinBuiltinAnyPackageSid, “APPLICATION PACKAGE AUTHORITY\ALL APPLICATION PACKAGES”.
# The self-documenting NTAccount type results in an object that “cannot be translated”.
$id = New-Object System.Security.Principal.SecurityIdentifier(“S-1-15-2-1”)
New-Object System.Security.AccessControl.RegistryAccessRule($id,
[System.Security.AccessControl.RegistryRights]::FullControl,
[System.Security.AccessControl.InheritanceFlags]::ContainerInherit,
[System.Security.AccessControl.PropagationFlags]::None,
[System.Security.AccessControl.AccessControlType]::Allow)
}
function GrantRequiredAccess($key) {
$acl = Get-Acl $key
$acl.AddAccessRule((MakeACE))
Set-Acl $key $acl
}
# All Windows 10, since Microsoft apparently managed to break build 10240 as well in December 2015, after having shipped 10586 broken from the start.
#New-EventLog –LogName Application –Source “LogonScript”
#Write-EventLog -LogName Application -Source LogonScript -EntryType Information -EventId 1 -Message “In LoginScript to fix roaming profiles”
if ([Environment]::OSVersion.Version.Major -eq 10) {
# Write-EventLog -LogName Application -Source LongScript -EntryType Information -EventId 1 -Message “Windows 10 detected”
GrantRequiredAccess “HKCU:\Software\Classes\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.microsoftedge_8wekyb3d8bbwe”
GrantRequiredAccess “HKCU:\SOFTWARE\Classes\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.cortana_cw5n1h2txyewy”
Step3
“ExcludeProfileDirs” Registry Tweak
- Continue Editing the above mentioned GPO.
- Navigate to: User Configuration > Preferences->Windows Settings->Registry, new registry item. Put the following information
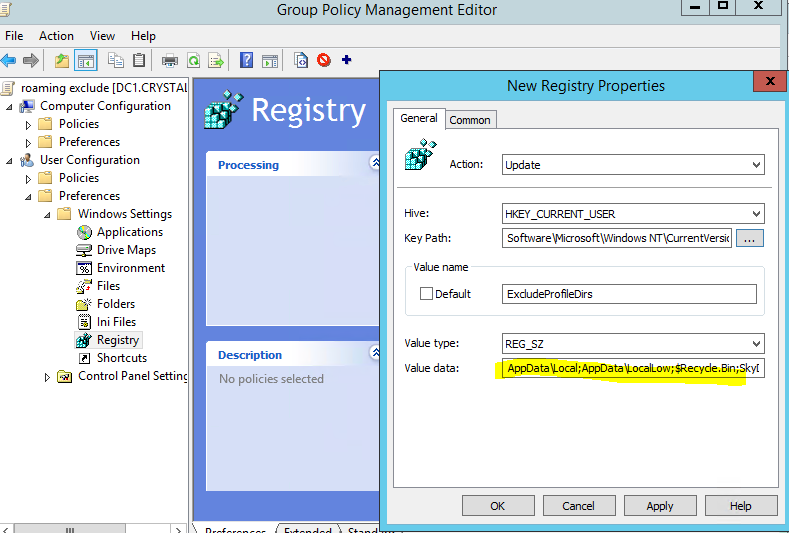
The key path is:
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon (don’t copy-paste it, navigate yourself to it!!!!)
On the Value data field you should include the following to support Windows 10 version 1703.
AppData\LocalLow;$Recycle.Bin;OneDrive;WorkFolders;AppData\Local\Comms;AppData\Local\ConnectedDevicesPlatform;AppData\Local\Google;AppData\Local\GroupPolicy;AppData\Local\Mozilla;AppData\Local\Packages;AppData\Local\Publishers;AppData\Local\PeerDistRepub;AppData\Local\Temp;AppData\Local\VirtualStore;AppData\Local\Winternals;AppData\Local\Adobe;AppData\Local\Apple;AppData\Local\AppleComputer;AppData\Local\Autodesk;AppData\Local\Chromium;AppData\Local\CrashDumps;AppData\Local\NVIDIA;AppData\Local\NVIDIACorporation;AppData\Local\Skype;AppData\Local\WebEx;AppData\Local\Foxit Reader;AppData\Local\Macromedia;AppData\Local\Microsoft_Corporation;AppData\Local\Real;AppData\Local\DropBox;AppData\Local\Vmware;AppData\Local\Windows Live;AppData\Local\CrashDumps;AppData\Local\Citrix;AppData\Local\Microsoft\AppV;AppData\Local\Microsoft\Credentials;AppData\Local\Microsoft\Feeds;AppData\Local\Microsoft\Feeds Cache;AppData\Local\Microsoft\GameDVR;AppData\Local\Microsoft\Group Policy;AppData\Local\Microsoft\InputPersonalization;AppData\Local\Microsoft\InstallAgent;AppData\Local\Microsoft\Internet Explorer;AppData\Local\Microsoft\Media Player;AppData\Local\Microsoft\OneDrive;AppData\Local\Microsoft\PenWorkspace;AppData\Local\Microsoft\PlayReady;AppData\Local\Microsoft\Vault;AppData\Local\Microsoft\Windows Live;AppData\Local\Microsoft\Windows Sidebar;AppData\Local\Microsoft\WindowsApps;AppData\Local\Microsoft\Windows\UPPS;AppData\Local\Microsoft\Windows\1033;AppData\Local\Microsoft\Windows\ActionCenterCache;AppData\Local\Microsoft\Windows\Application Shortcuts;AppData\Local\Microsoft\Windows\Burn;AppData\Local\Microsoft\Windows\GameExplorer;AppData\Local\Microsoft\Windows\History;AppData\Local\Microsoft\Windows\IECompatCache;AppData\Local\Microsoft\Windows\IECompatUaCache;AppData\Local\Microsoft\Windows\INetCache;AppData\Local\Microsoft\Windows\INetCookies;AppData\Local\Microsoft\Windows\Notifications;AppData\Local\Microsoft\Windows\OfflineFiles;AppData\Local\Microsoft\Windows\PowerShell;AppData\Local\Microsoft\Windows\PRICache;AppData\Local\Microsoft\Windows\Ringtones;AppData\Local\Microsoft\Windows\RoamingTiles;AppData\Local\Microsoft\Windows\Safety;AppData\Local\Microsoft\Windows\SchCache;AppData\Local\Microsoft\Windows\SettingSync;AppData\Local\Microsoft\Windows\Shell;AppData\Local\Microsoft\Windows\WebCache;AppData\Local\Microsoft\Windows\WER;AppData\Local\Microsoft\Windows\Explorer;AppData\Local\Microsoft\CLR_v4.0;AppData\Local\Microsoft\CLR_v4.0_32
Step4
Continue editing the above group policy for the Applocker part.
Computer Configuration > Policies > Windows Settings > Security Settings > Application Control Policies > AppLocker > Packaged App Rules > Right Click and create Default rules.
Step5
You should now force the group policy update on the problematic WKS (using gpupdate /force via cmd), log off and log on a few times. We had cases that we had to remove the roaming profile and reissue it again for this to work.
The above workaround is a merge of various articles and blog outputs we found on the web, while trying to solve an issue like this. The solution came after applying all of the above, and not one or the other.
Credits and references go to:
- Dr James Bayley’s excellent article https://blog.jamesbayley.com/2016/02/10/fixed-windows-10-roaming-profiles-break-edge-and-other-packaged-applications/
- https://social.technet.microsoft.com/Forums/en-US/fd436515-6423-4015-9afe-d7e6034909ab/windows-10-threshold-2-edgesearch-issues-for-domain-joined-pcs?forum=win10itprogeneral
- https://partnersupport.microsoft.com/en-us/par_clientsol/forum/par_win/roaming-profile-in-windows-10/173fffe7-6751-4721-a19c-c164a4658b90?auth=1
- https://www.youtube.com/watch?v=R4R4QlExLsU